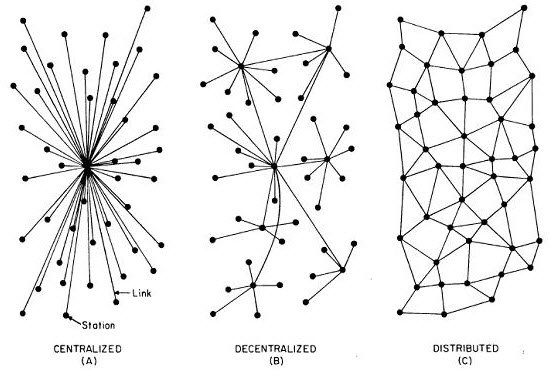
In this article, I will focus and talk more about Meganet, which has been in the news. It is a decentralized Internet structure.
What is Meganet
Most of you might have heard of Kim Schmitz (aka Kim Dotcom). He is a well-known, wanted hacker on the Internet. He is the founder of Megaupload and certain other websites that have the Internet police on their heels to deport him to the US and try him for different Internet crimes. After Kim Dotcom’s Megaupload was taken down, the German hacker and Internet entrepreneur turned his attention to an Internet that the government cannot control, nor can corporations snoop on what the users are doing. The decentralized Internet model is not very clear at this moment, but it won’t be tied to IP addresses. It will clear any government or corporate agencies wanting to know what you have been doing on your Internet. Currently, the model – though not explained entirely – is open for crowdfunding, and Kim Dotcom says he will launch it on the anniversary of the government taking his Megaupload site down. He also says that though the initial reception of the model may not be much, ten years from now, the concept will be understood by everyone, and there will be more and more people (users) opting in for the decentralized Internet he names Meganet. He claims that the model will work so that no one except the user can know what they are doing on the Internet. That is a big claim, and it requires volunteers to be accomplished. There are many benefits, privacy being the foremost, which makes Kim Dotcom believe that many people will come forward and start using Meganet.
How does Decentralized Internet work
This section has been created based on the many articles and threads on the decentralized Internet. These communications were enough to give me a rough idea of how the decentralized Internet will work. People using mobile devices do not know how much of their bandwidth lies idle and is never used. Decentralized Internet will use this bandwidth to provide Internet to everyone who signs up for it. The current Internet will be just a stub so people can launch the decentralized Internet and then go worry-free. There are no direct costs involved except for the costs of data transfer on mobile devices. Meganet’s founder says that Meganet will not drain off the users’ batteries using Meganet – while transferring or forwarding data packets from one device to another. To put it in one line, you as a user will be both a client and a server. Your devices will use idle bandwidth on other connected mobile devices and, in return, will provide bandwidth of your device to others. There won’t be hacking possibilities even though the devices will be interconnected. I am yet to find a solid backup to this statement. Like the TOR network, the connection may be a maze so that no one knows the IP address of where the Internet data packets are originating. Though it was in the news that TOR users can be figured out, Kim Dotcom is confident that his model has ample precautions to keep Meganet’s users happy and private. Since there won’t be any need for government servers or ISP-provided DNS resolvers, they won’t be able to tap into the network, and thus, the power of a decentralized Internet would be in the users’ hands. ZeroNet is another decentralized Internet that aims to deliver a decentralized web platform using Bitcoin cryptography and the BitTorrent network. Project Maelstorm is a P2P Network to host websites. Maidsafe is an open-source program hosted on GitHub that enables a decentralized Internet platform. Now read: What is Darknet or Deepnet?
Is decentralized Internet safe?
It would be difficult for hackers to discover and breach a secure server network with decentralized protocols. Data security isn’t the only benefit of decentralized networks. As well as remaining in your control, they ensure that your data stays safe.
What is the issue with decentralized network processing?
It is important for decentralized networks to replicate and coordinate among multiple servers, so any errors or interruptions in this process may cause security concerns or service issues.